You know you need to lock up your doors, keep your valuables safe and an eye on your bag in a busy subway or crowded space. Security comes easy to us in our daily lives. But what about security online?
For many of us, it’s not as natural. How much do you think about internet security? Are you confident in your knowledge about how to keep you, your members and your organization safe from cyber-attacks?
No worries. We’re exploring the basic here to get you started on your cyber security journey.
What is cyber security?
Also called information tech security, internet security or digital security, cyber security refers to keeping your computers, systems, information, networks and data safe in the digital space. When we say “safe”, we mean safe from digital attacks like computer viruses or hacking, but also from people gaining access to your accounts by stealing your passwords or even stealing personal information like your credit card info.
The challenging world of cyber security
The security around your house is made easier with tech. Cameras let you keep an eye on your property while you’re gone (especially ones that you can access on your phone) and lock systems have grown more and more advanced. With digital cyber security, it’s harder to keep up with all the changes.
People who hack systems or attack cyber systems can use coding and other digital tools in ways that many of us can’t understand. And it gets more in-depth and complicated as tech advances. It’s a whole other threat that can feel harder to protect against – especially if you’re not a tech wiz.
Did you know…
- It can take more than 190 days on average to identify a data breach
- The number of cyber-attacks is rising, with 15.1% more attacks in 2021 than in 2020
- The most common sources of cyber-attacks are phishing (20%) and malware (22%)
These stats (from Forbes) show just how important it is to educate yourself about cyber security. But they also prove that small steps can help keep you protected. You’d be surprised how some simple practices can keep you (and your members) protected.
Malware and phishing
Because these are the most common types of cyber-attacks, we want to look at them a bit deeper.
Phishing
Phishing is the act of sending out a bunch of emails to try to get someone to open a document with a virus (malware!), to send personal information back or to give the hacker access to the computer. This type of cyber attack involves creating emails that look like they come from a reputable source like Amazon, the government or other well-known brands, or can be totally made-up stories or warnings trying to scare people into giving out information.
It’s called phishing because they cast out a large net of emails and “fish” for people to respond. It’s one of the most low-effort cyber-attacks out there because hackers can send out plenty of emails in a short period of time with little effort.
Examples of phishing emails
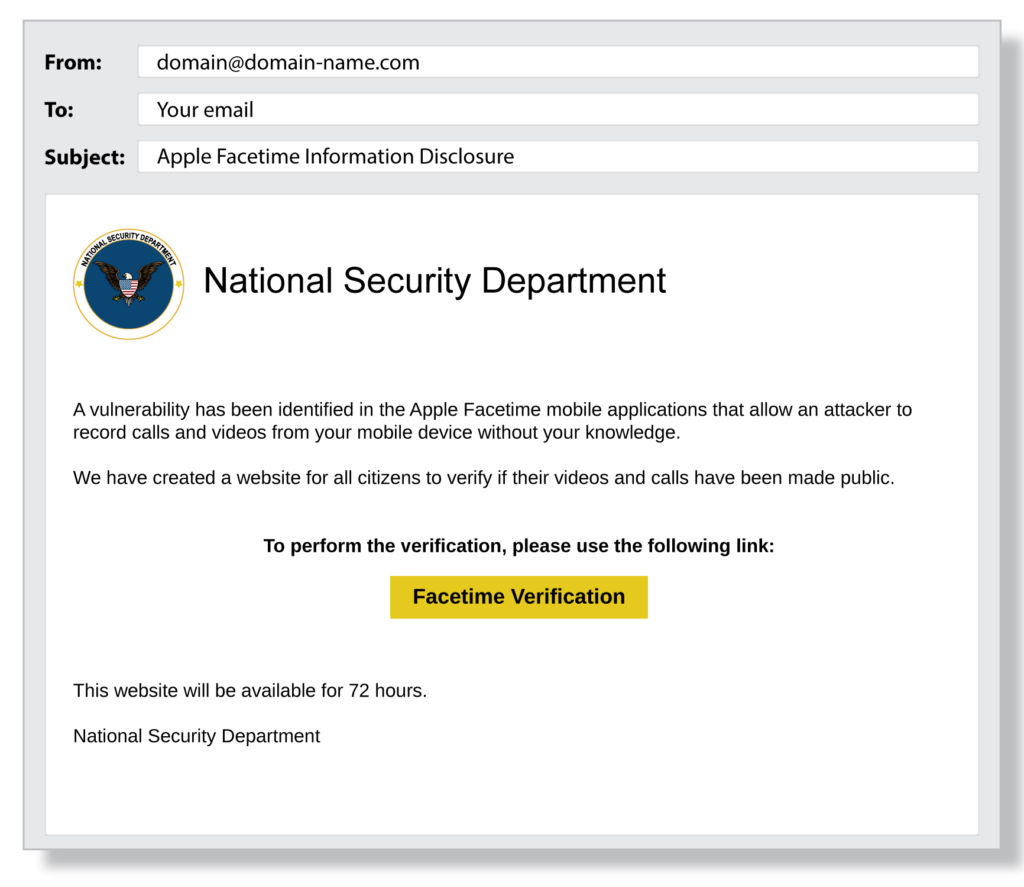
Look at the email alone. Notice the generic from email. Does it make sense that the national security department would email about an Apple issue? Does the reason for the email sound legit?
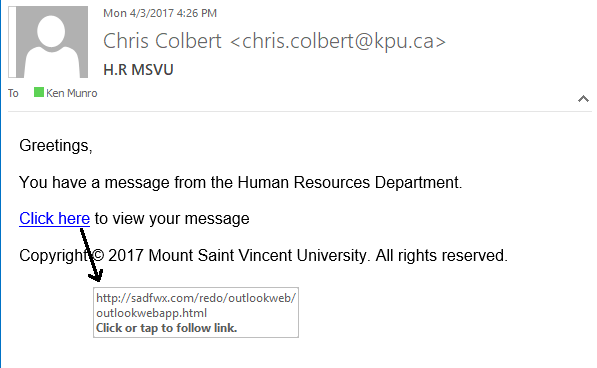
This is another example of a phishing email. Notice that the link URL is http (which we talk about below) and goes to a super generic and strange looking URL. (You can view linked URLS by hovering over them or right clicking, copying the link and pasting it without clicking on it to view it.
In this example, the copyright seem strange, and it doesn’t make sense for an HR department to send a generic email which then links to another message.
This email is a perfect example of how to use and trust your gut for phishing emails.
Malware
Malware is software created to disrupt, damage or delete information on your computer, or to give someone access to your computer without you knowing. It can be downloaded from a document, email, website or any other source. In specific cases, it can also be uploaded from an external drive.
As mentioned above, it can be included as a download in a phishing email, so these two really go hand in hand.
Cyber security for phishing and malware (and other cyber-attacks)
One of the best ways to protect yourself (and your members) from these common attacks is to be wary of any suspicious emails that come in. Do not open an email or click on any links if:
- You do not recognize the sender
- There are common spelling mistakes or grammar mistakes in the email
- The links don’t look like regular URLS
- Logos, names or other brand info look strange (especially if the sender email address doesn’t match)
- It is prompting you to send back or share personal information like bank account numbers, social security info, credit card into, passwords, etc.
- The email tries to trick you into a panic by using words like “WARNING”, “immediate”, “threat” or “consequences”
Really, trust your gut. It’s always better to error on the side of caution.
If you see a strange email, report it to your IT department if you have one. Don’t have an IT department? You can report the email and delete it. If it is a legit email, the sender will reach out again.
Google has some great resources on phishing here. Outlook does as well, here.
Other ways to upgrade your cyber security
Unfortunately, many hackers and cyber attackers want easy targets. The good news? By taking some simple and easy-to-do steps to upgrade your security, you can make it just a little bit harder to target your organization in a cyber-attack. This can be all it takes to keep you safe.
Make sure your website is HTTPS
If you look at a URL, “the www.” is often proceeded by “https://”. Back in the 1990s, it used to be “http://” without the S. The S was added to indicate that “Secure Socket Layer” protocol (or SSL) is added to the website to keep it protected from cyber-attacks. It was first used for web pages where people would put in credit card or other sensitive info. Now, it’s common practise for every website to have HTTPS protocol for added security.
Check out your own website. Is it https? (In Google Chrome, this is also shown by a little lock to the left of the URL.)
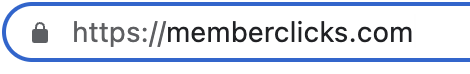
If it is not, reach out to your website or AMS provider and ask about how you swap over. Some AMS providers, like us here at MemberClicks, have made it a priority to have all new websites be HTTPS and to get all existing client websites over to HTTPS.
Change your passwords regularly and don’t pick easy-to-guess ones
We know how hard it can be to keep track of passwords when you change them all the time, but it really is a good idea to keep on top of this practice. Changing your password every few months – especially your AMS or member database password – can help keep you protected.
And, when changing your passwords, get creative each time. Use the rules of numbers, special characters and whole new passwords for each time. Repeat passwords may be easier to remember, but they can also be easier to hack.
A great tip? Pick something that you love and try to keep it around that.
For example, if you love football, “FootballRulez” isn’t a great password but “F0ot8@llRu13z(!)” is much is harder to guess.
Using a mix of symbols, letters and words can make it easier to remember but harder to hack.
The little things matter in cyber security
Your password, email opening habits and site security really are the three best places to get started in your cyber security journey. Don’t underestimate the power that little changes can make to keep your cyber security safe.
Keep learning (and teach your members)
Consider including some articles and resources about cyber security in your newsletters or member communications to educate your members. You can also share it internally with your team. Here’s a few of our favourite cyber security resources
- Cybrary – free courses with the goal of educating as many people as possible about this topic
- Google tips for creating strong passwords
- More info on phishing scams by the Federal Trade Commission
















